AWS Quick Notes.
Tips (Quote from Questions)
- Use AWS Consolidated Billing by creating AWS Organizations to link the divisions accounts to a parent corporate account
- Enable IAM cross-account access for all corporate IT administrators in each child account
- there is no cost if the instance is running and it has only one associated ElasticIP
- AWS Elastic Beanstalk stores your application files and optionally, server log files in Amazon S3
- By using (Docker with) Elastic Beanstalk, you have an infrastructure that automatically handles the details of capacity provisioning, load balancing, scaling, and application health monitoring.
- The default timeout is 3 seconds and the maximum execution duration per request in AWS Lambda is 900 seconds, which is equivalent to 15 minutes.
- If Lambda concurrency limit is exceeded, the function will be throttled but not terminated, which is in contrast with what is happening in the scenario.
- S3 versioning
- Versioning enables you to control which file a request returns even when the user has a version cached either locally or behind a corporate caching proxy.
- CloudFront access logs include the names of your files, so versioning makes it easier to analyze the results of file changes.
- Versioning provides a way to serve different versions of files to different users.
- Versioning simplifies rolling forward and back between file revisions.
- Versioning is less expensive
- CloudFormation
- A CloudFormation stack set lets you create stacks in AWS accounts across regions by using a single CloudFormation template. All the resources included in each stack are defined by the stack set’s CloudFormation template. As you create the stack set, you specify the template to use, as well as any parameters and capabilities that the template requires.
- JSON Format
- Format Version
- Description
- Metadata
- Parameters
- Mappings
- Conditions
- Transform
- Resources (Required)
- Outputs
- Event Sourcing Application with Kinesis FireHose
- Event sourcing heavily relies on the persistence of events so it can rebuild/replay the state of your application at any given point in time in the past. Among the options given, Amazon Kinesis Data Firehose is the most suitable service to stream data as it provides an ordering of records, as well as the ability to read and/or replay records in the same order.
- Application Load Balancers/Route53 support Weighted Target Groups routing
- Outputs is an optional section of the CloudFormation template that describes the values that are returned whenever you view your stack’s properties
- Enable Enhanced Networking with Elastic Network Adapter (ENA) on the Windows EC2 Instances. Linux, maybe EFA
- If you do not have an Amazon Aurora Replica (i.e. single instance) and are not running Aurora Serverless, Aurora will attempt to create a new DB Instance in the same Availability Zone as the original instance.
- By default, CloudTrail event log files are encrypted using Amazon S3 server-side encryption (SSE).
- Amazon SQS automatically deletes messages that have been in a queue for more than the maximum message retention period. The default message retention period is 4 days. ~ 14
- AWS Trusted Advisor is an online tool that provides you real-time guidance to help you provision your resources following AWS best practices. It inspects your AWS environment and makes recommendations for saving money, improving system performance and reliability, or closing security gaps.
- Amazon S3 now provides increased performance to support at least 3,500 requests per second to add data and 5,500 requests per second to retrieve data, which can save significant processing time for no additional charge.
- AWS OpsWorks is a configuration management service that provides managed instances of Chef and Puppet. Chef and Puppet are automation platforms that allow you to use code to automate the configurations of your servers.
- IAM roles are global service that are available to all regions hence, all you must do is assign the existing IAM role to the instance in the new region.
- Remember that for S3 and DynamoDB service, you must use a Gateway VPC Endpoint and not an Interface VPC Endpoint.
- CNAME records cannot be created for your zone apex.
- The EBS volume
- can be used while the snapshot is in progress
- snapshots are automatically encrypted
- all data moving between the volume and the instance are encrypted
- You can use AWS X-Ray to trace and analyze user requests as they travel through your Amazon API Gateway APIs to the underlying services.
- API Gateway supports AWS X-Ray tracing for all API Gateway endpoint types: regional, edge-optimized, and private.
- You can use AWS X-Ray with Amazon API Gateway in all regions where X-Ray is available.
- SWF is incorrect because this is a fully-managed state tracker and task coordinator service. It does not provide serverless orchestration to multiple AWS resources.
- never duplicated, assigned only once
- An Elastic Fabric Adapter (EFA) is a network device that you can attach to your Amazon EC2 instance to accelerate High Performance Computing (HPC) and machine learning applications.
- To ensure that a Classic Load Balancer stops sending requests to instances that are de-registering or unhealthy while keeping the existing connections open, use connection draining.
- SQS FIFO
- order is critical
- duplicates can’t be tolerated
- RDS Enhanced Monitoring Metrics
- RDS (child) processes
- OS processes
- You can configure Amazon Redshift to copy snapshots for a cluster to another region. To configure cross-region snapshot copy, you need to enable this copy feature for each cluster and configure where to copy snapshots and how long to keep copied automated snapshots in the destination region. When cross-region copy is enabled for a cluster, all new manual and automatic snapshots are copied to the specified region.
- an Origin Access Identity (OAI) is a CloudFront feature used in conjunction with Amazon S3 buckets to control access to the objects (files) in your bucket. OAC
- With AWS Site-to-Site VPN, you can connect to an Amazon VPC in the cloud the same way you connect to your branches. AWS Site-to- Site VPN establishes secure and private sessions with IP Security (IPSec) and Transport Layer Security (TLS) tunnels.
- Since only EBS- backed instances can be stopped and restarted, it is implied that the instance is EBS-backed. Remember that an instance store-backed instance can only be rebooted or terminated, and its data will be erased if the EC2 instance is either stopped or terminated.
- There is a vCPU-based On-Demand Instance limit per region which is why subsequent requests failed. Just submit the limit increase form to AWS and retry the failed requests once approved.
- You can perform S3 Select to query only the necessary data inside the CSV files based on the bucket’s name and the object’s key.
- A Kinesis data stream stores records from 24 hours by default to a maximum of 168 hours.
- When a Kinesis data stream is configured as the source of a Firehose delivery stream, Firehose’s PutRecord and PutRecordBatch operations are disabled and Kinesis Agent cannot write to Firehose delivery stream directly. Data needs to be added to the Kinesis data stream through the Kinesis Data Streams PutRecord and PutRecords operations instead.
- A VPC endpoint enables you to privately connect your VPC to supported AWS services and VPC endpoint services powered by AWS PrivateLink without requiring an internet gateway, NAT device, VPN connection, or AWS Direct Connect connection. Instances in your VPC do not require public IP addresses to communicate with resources in the service. Traffic between your VPC and the other service does not leave the Amazon network.
- Using Amazon Redshift Spectrum, you can efficiently query and retrieve structured and semistructured data from files in Amazon S3 without having to load the data into Amazon Redshift tables.
- An S3 Glacier vault is a container for storing archives. When you create a vault, you specify a vault name and the AWS Region in which you want to create the vault. S3 Glacier Vault Lock allows you to easily deploy and enforce compliance controls for individual S3 Glacier vaults with a vault lock policy. You can specify controls such as “write once read many” (WORM) in a vault lock policy and lock the policy from future edits.
- Minimum 30-Day Storage Charge for S3 Standard-IA and S3 One Zone-IA which makes it not most-cost-efficient
- WAF log destination
- CloudWatch logs
- S3
- Kinesis data firehose
- As the Availability Zones got unbalanced, Amazon EC2 Auto Scaling will compensate by rebalancing the Availability Zones. When rebalancing, Amazon EC2 Auto Scaling launches new instances before terminating the old ones, so that rebalancing does not compromise the performance or availability of your application
- Amazon EC2 Auto Scaling creates a new scaling activity for terminating the unhealthy instance and then terminates it. Later, another scaling activity launches a new instance to replace the terminated instance
- The end-to-end time to transfer up to 80 TB of data into AWS with Snowball Edge is approximately one week, including the usual shipping and handling time in AWS data centers.
- You must use a public virtual interface from the Direct Connect connection to connect to an S3 bucket.
- KDS - With enhanced fan-out developers can register stream consumers to use enhanced fan-out and receive their own 2MB/second pipe of read throughput per shard, and this throughput automatically scales with the number of shards in a stream.
- PHP is not supported by Lambda.
- The
AWS-ApplyPatchBaselineSSM document supports patching on Windows instances only and doesn’t support Linux instances. For applying patch baselines to both Windows Server and Linux instances, the recommended SSM document isAWS-RunPatchBaseline. - When you create a launch configuration, the default value for the instance placement tenancy is null and the instance tenancy is controlled by the tenancy attribute of the VPC. If you set the Launch Configuration Tenancy to default and the VPC Tenancy is set to dedicated, then the instances have dedicated tenancy. If you set the Launch Configuration Tenancy to dedicated and the VPC Tenancy is set to default, then again the instances have dedicated tenancy.
- storage pricing
- EFS - pay only for the resources you use. EFS Standard 0.3 per GB per month
- EBS - pay for what you provisioned. EBS GP2, 0.10 per GB per month
- S3 - pay what you use. S3 Standard 0.023 per GB per month
- Multi-AZ follows synchronous replication and spans at least two Availability Zones within a single region. Read Replicas follow asynchronous replication and can be within an Availability Zone, Cross-AZ, or Cross-Region
- AWS recommends that you should use Snowmobile to migrate large datasets of 10PB or more in a single location. For datasets less than 10PB or distributed in multiple locations, you should use Snowball.
- Create a snapshot copy grant in the destination Region for a KMS key in the destination Region. Configure Redshift cross-Region snapshots in the source Region
- Lambda
- By default, Lambda functions always operate from an AWS-owned VPC and hence have access to any public internet address or public AWS APIs. Once a Lambda function is VPC-enabled, it will need a route through a NAT gateway in a public subnet to access public resources
- Since Lambda functions can scale extremely quickly, it’s a good idea to deploy a CloudWatch Alarm that notifies your team when function metrics such as ConcurrentExecutions or Invocations exceeds the expected threshold
- If you intend to reuse code in more than one Lambda function, you should consider creating a Lambda Layer for the reusable code
- Use message timers to postpone the delivery of certain messages to the queue by one minute
- SCP
- If a user or role has an IAM permission policy that grants access to an action that is either not allowed or explicitly denied by the applicable SCPs, the user or role can’t perform that action
- SCPs affect all users and roles in attached accounts, including the root user
- SCPs do not affect service-linked role
- AWS Artifact is your go-to, central resource for compliance-related information that matters to you. It provides on-demand access to AWS’ security and compliance reports and select online agreements. Reports available in AWS Artifact include our Service Organization Control (SOC) reports, Payment Card Industry (PCI) reports, and certifications from accreditation bodies across geographies and compliance verticals that validate the implementation and operating effectiveness of AWS security controls.
- Custom Metrics - cloud-watch & EC2
- memory
- disk swap
- disk space
- page file
- log collection
- You can authenticate to your DB instance using AWS Identity and Access Management (IAM) database authentication. IAM database authentication works with MySQL and PostgreSQL. With this authentication method, you don’t need to use a password when you connect to a DB instance. Instead, you use an authentication token.
- Network traffic to and from the database is encrypted using Secure Sockets Layer (SSL).
- You can use IAM to centrally manage access to your database resources, instead of managing access individually on each DB instance.
- For applications running on Amazon EC2, you can use profile credentials specific to your EC2 instance to access your database instead of a password, for greater security
- AWS Resource Access Manager (RAM) is a service that enables you to easily and securely share AWS resources with any AWS account or within your AWS Organization. You can share AWS Transit Gateways, Subnets, AWS License Manager configurations, and Amazon Route 53 Resolver rules resources with RAM.
- AWS Control Tower simply offers the easiest way to set up and govern a new, secure, multi-account AWS environment.
- Authenticate the users using Redis AUTH by creating a new Redis Cluster with both the
--transit-encryption-enabledand--auth-tokenparameters enabled. - ASG behavior
- If there are instances in multiple Availability Zones, choose the Availability Zone with the most instances and at least one instance that is not protected from scale in. If there is more than one Availability Zone with this number of instances, choose the Availability Zone with the instances that use the oldest launch template.
- Determine which unprotected instances in the selected Availability Zone use the oldest launch template. If there is one such instance, terminate it.
- If there are multiple instances to terminate based on the above criteria, determine which unprotected instances are closest to the next billing hour. (This helps you maximize the use of your EC2 instances and manage your Amazon EC2 usage costs.) If there is one such instance, terminate it.
- If there is more than one unprotected instance closest to the next billing hour, choose one of these instances at random.
- A NAT Gateway is a highly available, managed Network Address Translation (NAT) service for your resources in a private subnet to access the Internet. NAT gateway is created in a specific Availability Zone and implemented with redundancy in that zone.
- Amazon S3 delivers strong read-after-write consistency automatically, without changes to performance or availability, without sacrificing regional isolation for applications, and at no additional cost.
- You can only use a launch template to provision capacity across multiple instance types using both On-Demand Instances and Spot Instances to achieve the desired scale, performance, and cost You cannot use a launch configuration to provision capacity across multiple instance types using both On-Demand Instances and Spot Instances.
- AWS S3 console cannot be used to copy 1 petabytes of data from one bucket to another as it’s not feasible.
- RDS auto backup retention period is only 35 days. We could consider AWS Backup.
- you cannot directly download or export an automated snapshot in RDS to s3
- every subnet that you create is automatically associated with the main route table for the VPC
- EC2
- only EBS-backed instances can be stopped and restarted
- an instance store-backed instance can only be rebooted or terminated, and its data will be erased if the EC2 instance is either stopped or terminated
- ElasticIP will be disassociated from the instance if it is an EC2-Classic instance. Otherwise, if it is an EC2-VPC instance, the ElasticIP remains associated
- Use an Amazon SQS queue to decouple the application components and scale-out the EC2 instances based upon the
ApproximateNumberOfMessagesmetric in Amazon CloudWatch. - VPC peering does not support transitive peering relationships.
- DynamoDB
- cannot integrate DynamoDB table with CloudFront as these two are incompatible
- by default, auto scaling is not enabled in an DynamoDB table, which is created using the AWS CLI
- Organization
- an SCP can only be attached to the organization root, to an organizational unit (OU), or directly to an account, but not directly in the IAM User.
- Use AWS Database Migration Service (AWS DMS) to migrate data from the existing DB cluster to a new Aurora Serverless database.
- Kinesis
- A Kinesis data stream stores records from 24 hours by default to a maximum of 8760 hours (365 days).
- RDS Storage Auto Scaling automatically scales storage capacity in response to growing database workloads, with zero downtime.
- You can associate the
CreationPolicyattribute with a resource to prevent its status from reaching create complete until AWS CloudFormation receives a specified number of success signals or the timeout period is exceeded. To signal a resource, you can use the cfn-signal helper script or SignalResource API. AWS CloudFormation publishes valid signals to the stack events so that you track the number of signals sent. - the cfn-init helper script is not suitable to be used to signal another resource, use cfn-signal instead.
- You can perform S3 Select to query only the necessary data inside the CSV files based on the bucket’s name and the object’s key.
- Parameter Store provides secure, hierarchical storage for configuration data and secrets management. & It is possible to store encrypted parameters on Secrets Manager, however, there is a cost associated with using this service.
- Implementation begins by installing the AWS Replication Agent on your source servers. When you launch Test or Cutover instances, AWS Application Migration Service automatically converts your source servers to boot and runs natively on AWS.
- The AWS Application Discovery Service is primarily used to track the migration status of your on-premises applications from the Migration Hub console in your home Region. This service is not capable of doing the actual migration.
- Amazon EKS supports two autoscaling solutions:
- Karpenter is a flexible, high-performance Kubernetes cluster autoscaler that launches appropriately sized compute resources, like Amazon EC2 instances, in response to changing application load. It integrates with AWS to provision compute resources that precisely match workload requirements.
- Cluster Autoscaler, on the other hand, automatically adjusts the number of nodes in a cluster based on pod failures or rescheduling. It utilizes Auto Scaling groups for managing the cluster’s node capacity.
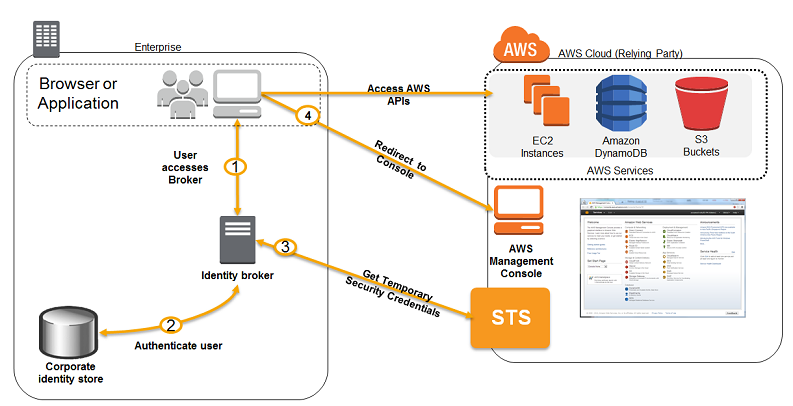
- If your identity store is not compatible with SAML 2.0 then you can build a custom identity broker application to perform a similar function. The broker application authenticates users, requests temporary credentials for users from AWS, and then provides them to the user to access AWS resources.
- to resolve SQS message processed twice
- replace SQS with AWS Step Functions
- use SQS FIFO Queue
- You can configure Amazon Redshift to copy snapshots for a cluster to another region. To configure cross-region snapshot copy, you need to enable this copy feature for each cluster and configure where to copy snapshots and how long to keep copied automated snapshots in the destination region. When a cross-region copy is enabled for a cluster, all new manual and automatic snapshots are copied to the specified region.
- RDS enhanced monitoring
- OS processes
- RDS child processes
- Access to your cluster using AWS Identity and Access Management (IAM) entities is enabled by the AWS IAM Authenticator for Kubernetes, which runs on the Amazon EKS control plane. The authenticator gets its configuration information from the
aws-authConfigMap(AWS authenticator configuration map). - By default, CloudTrail event log files are encrypted using Amazon S3 server-side encryption (SSE).
- (EBS) Snapshots occur asynchronously; the point-in-time snapshot is created immediately, but the status of the snapshot is
pendinguntil the snapshot is complete (when all of the modified blocks have been transferred to Amazon S3), which can take several hours for large initial snapshots or subsequent snapshots where many blocks have changed. - You can use Amazon Data Lifecycle Manager (Amazon DLM) to automate the creation, retention, and deletion of snapshots taken to back up your Amazon EBS volumes.
- AWS Secret manager is costly than AWS System Manager Parameter Store. choose the second if You are going to save application configs
- Every subnet that you create is automatically associated with the main route table for the VPC.
- aurora failover strategy
- If you have an Amazon Aurora Replica in the same or a different Availability Zone, when failing over, Amazon Aurora flips the canonical name record (CNAME) for your DB Instance to point at the healthy replica, which in turn is promoted to become the new primary. Start-to-finish failover typically completes within 30 seconds.
- If you are running Aurora Serverless and the DB instance or AZ becomes unavailable, Aurora will automatically recreate the DB instance in a different AZ.
- If you do not have an Amazon Aurora Replica (i.e., single instance) and are not running Aurora Serverless, Aurora will attempt to create a new DB Instance in the same Availability Zone as the original instance. This replacement of the original instance is done on a best-effort basis and may not succeed, for example, if there is an issue that is broadly affecting the Availability Zone.
- The only solution that works for both existing and future member accounts is to apply a Deny policy to the root of the organization. When you attach a policy to the organization root, all OUs and accounts in the organization inherit that policy which ensures that any new accounts that are added will inherit the policy automatically.
- migration plan
- AWS Application Discovery Service performs server utilization data and dependency mapping and collects and presents configuration, usage, and behavior data from your servers to help you better understand your workloads.
- You can export this data as a CSV file and use it to estimate the Total Cost of Ownership (TCO) of running on AWS and to plan your migration to AWS. In addition, this data is also available in AWS Migration Hub, where you can migrate the discovered servers and track their progress as they get migrated to AWS.
- The AWS Cloud Adoption Readiness Tool (CART) helps organizations of all sizes develop efficient and effective plans for cloud adoption and enterprise cloud migrations. This 16-question online survey and assessment report details your cloud migration readiness across six perspectives including business, people, process, platform, operations, and security.
- Since SCPs only allow or deny the use of an AWS service, you don’t want to block OUs from completely using the EC2 service. Thus, you will need to provide cross-account access and the IAM policy to every member accounts of the OU.
- Beanstalk
- AWS Elastic Beanstalk provides several options for how deployments are processed, including deployment policies (All at once, Rolling, Rolling with additional batch, and Immutable) and options that let you configure the batch size and health check behavior during deployments.
- With rolling deployments, Elastic Beanstalk splits the environment’s EC2 instances into batches and deploys the new version of the application to one batch at a time, leaving the rest of the instances in the environment running the old version of the application. During a rolling deployment, some instances serve requests with the old version of the application, while instances in completed batches serve other requests with the new version.
- Immutable deployments perform an immutable update to launch a full set of new instances running the new version of the application in a separate Auto Scaling group alongside the instances running the old version. Immutable deployments can prevent issues caused by partially completed rolling deployments. If the new instances don’t pass health checks, Elastic Beanstalk terminates them, leaving the original instances untouched.
- Note that you can’t use a self-signed certificate for HTTPS communication between CloudFront and your origin.
- There is no default SSL certificate in ELB, unlike what we have in CloudFront (*.cloudfront.net).
- When you create an interface or gateway endpoint, you can attach an endpoint policy to it that controls access to the service to which you are connecting. Endpoint policies must be written in JSON format. Not all services support endpoint policies.
- Restoring 40 TB of data may not be possible if you have an RTO requirement of 30 minutes. Depending on how busy the database was during the time the snapshot was taken, the restoration process may take longer than 30 minutes to complete. Moreover, automated backups only occur once every day during the defined backup window. You can’t configure it to run every 5 minutes.
- Remember that only one virtual private gateway (VGW) can be attached to a VPC at a time.
- AWS Config
- Evaluate your AWS resource configurations for desired settings.
- Get a snapshot of the current configurations of the supported resources that are associated with your AWS account.
- Retrieve configurations of one or more resources that exist in your account.
- Retrieve historical configurations of one or more resources.
- Receive a notification whenever a resource is created, modified, or deleted.
- View relationships between resources. For example, you might want to find all resources that use a particular security group.
- AWS Managed Policies
- For Administrators, you can use the AWS managed policy name: AdministratorAccess if you want to provision full access to a specific IAM User. This will enable the user to delegate permissions to every service and resource in AWS as this policy grants all actions for all AWS services and for all resources in the account.
- For Developer Power Users, you can use the AWS managed policy name: PowerUserAccess if you have users who perform application development tasks. This policy will enable them to create and configure resources and services that support AWS aware application development.
- You can add tags to resources when you create the resource. You can use the resource’s service console or API to add, change, or remove those tags one resource at a time. To add tags to—or edit or delete tags of—multiple resources at once, use Tag Editor. With Tag Editor, you search for the resources that you want to tag, and then manage tags for the resources in your search results.
- CloudFront
- HTTPS between viewers and CloudFront
- You can use a certificate that was issued by a trusted certificate authority (CA) such as Comodo, DigiCert, Symantec or other third-party providers.
- You can use a certificate provided by AWS Certificate Manager (ACM)
- HTTPS between CloudFront and a custom origin
- If the origin is not an ELB load balancer, such as Amazon EC2, the certificate must be issued by a trusted CA such as Comodo, DigiCert, Symantec or other third-party providers.
- If your origin is an ELB load balancer, you can also use a certificate provided by ACM.
- HTTPS between viewers and CloudFront
- When an invited account joins your organization, you do not automatically have full administrator control over the account, unlike created accounts. If you want the master account to have full administrative control over an invited member account, you must create the
OrganizationAccountAccessRoleIAM role in the member account and grant permission to the master account to assume the role. - Traffic Mirroring is an Amazon VPC feature that you can use to copy network traffic from an elastic network interface of Amazon EC2 instances. You can then send the traffic to out-of-band security and monitoring appliances for:
- Content inspection
- Threat monitoring
- Troubleshooting
- Follow these steps to configure a CloudFront web distribution to serve static content from an S3 bucket and dynamic content from a load balancer:
- Open your web distribution from the CloudFront console.
- Choose the Origins tab.
- Create one origin for your S3 bucket and another origin for your load balancer. Note: If you’re using a custom origin server or an S3 website endpoint, you must enter the origin’s domain name into the Origin Domain Name field.
- From your distribution, choose the Behaviors tab.
- Create a behavior that specifies a path pattern to route all static content requests to the S3 bucket. For example, you can set the “images/*.jpg” path pattern to route all requests for “.jpg” files in the images directory to the S3 bucket.
- Edit the Default (*) path pattern behavior and set its Origin as your load balancer.
- Use CloudFormation with Systems Manager Parameter Store to retrieve the latest AMI IDs for your template. Whenever you decide to update the EC2 instances, call the update-stack API in CloudFormation in your CloudFormation template.
- enabling RDS Proxy can further decrease the downtime of a failover to around 20 seconds (66% reduction from 60 seconds).
- Aurora Auto Scaling dynamically adjusts the number of Aurora Replicas provisioned for an Aurora DB cluster using single-master replication.
- Athena partition table is efficient than multiple bucket
- AWS Pipeline
- Store a container image in a repository – Amazon ECR can be used.
- Store the tool code in the repository – AWS CodeCommit can be used.
- Update the container image with the code and save back to repository – AWS CodeBuild can be used.
- Automate the whole process – AWS CodePipeline can be used to create an automated CI/CD pipeline.
Concepts
- AWS Organizations
- It allows you to consolidate multiple AWS accounts into an organization that you create and centrally manage. This makes it easier to organize accounts.
- You can create member accounts within the organization and invite existing accounts to join. This allows central management of accounts.
- AWS Organizations lets you organize accounts into groups and attach policy-based controls. This allows standardized access and resource policies across accounts.
- It provides consolidated billing so you can get a single bill for all accounts in your organization.
- Many AWS services like AWS Config, GuardDuty, Macie etc. can be centrally managed across multiple accounts using Organizations.
- Resources like IAM roles, policies can be shared across accounts making it easier to manage access.
- Overall AWS Organizations provides the infrastructure to easily build and centrally govern a multi-account environment on AWS.
- GuardDuty
- It continuously monitors AWS accounts and workloads for malicious or unauthorized behavior like escalation of privileges or communication with bad actors.
- GuardDuty analyzes log data from various AWS sources like CloudTrail, VPC flow logs, DNS logs etc to detect threats. It also processes features like Kubernetes audit logs, RDS login activity etc.
- It uses threat intelligence feeds and machine learning to identify anomalies and threats like compromised EC2 instances serving malware or unusual API calls.
- GuardDuty generates findings for any security issues detected. These findings can be viewed in the GuardDuty console or exported to S3.
- It provides protection for EKS workloads by monitoring Kubernetes audit logs for the EKS control plane through GuardDuty for EKS Protection feature.
- Being fully managed, there is no additional infrastructure required. GuardDuty operates independently without impacting workloads.
- Its integration with services like Security Hub and Detective allows centralized monitoring and investigation of findings.
- Amazon WorkSpaces is a fully managed desktop virtualization service that allows you to provision either Windows or Linux desktops in the AWS cloud.
- Certificates in ACM are Regional resources
- With AWS Global Accelerator, you can shift traffic gradually or all at once between the blue and the green environment and vice-versa without being subject to DNS caching on client devices and internet resolvers, traffic dials and endpoint weights changes are effective within seconds.
- You can share manual DB snapshots with up to 20 AWS accounts. Automated Amazon RDS snapshots cannot be shared directly with other AWS accounts.
- EBS Volumes
- When you create an EBS volume in an Availability Zone, it is automatically replicated within that zone to prevent data loss due to a failure of any single hardware component.
- An EBS volume can only be attached to one EC2 instance at a time.
- After you create a volume, you can attach it to any EC2 instance in the same Availability Zone
- An EBS volume is off-instance storage that can persist independently from the life of an instance. You can specify not to terminate the EBS volume when you terminate the EC2 instance during instance creation.
- EBS volumes support live configuration changes while in production which means that you can modify the volume type, volume size, and IOPS capacity without service interruptions.
- Amazon EBS encryption uses 256-bit Advanced Encryption Standard algorithms (AES-256)
- EBS Volumes offer 99.999% SLA.
- What are the prerequisites when routing traffic using Amazon Route 53 to a website that is hosted in an Amazon S3 Bucket?
- a registered domain name
- the s3 bucket name must be the same as the domain name
- RDS multi-AZ failover based on DNS - CNAME
- AWS
Fargate- AWS
Fargateis a server-less compute engine for containers that work with both Amazon Elastic Container Service (ECS) and Amazon Elastic Kubernetes Service (EKS). - by default,
Fargatetasks are given a minimum of 20 GiB of free ephemeral storage
- AWS
- AWS Application Migration Service (AWS MGN) is the primary migration service recommended for lift-and-shift migrations to AWS. AWS encourages customers who are currently using AWS Elastic Disaster Recovery to switch to AWS MGN for future migrations. AWS MGN enables organizations to move applications to AWS without having to make any changes to the applications, their architecture, or the migrated servers.
- AWS Health provides ongoing visibility into your resource performance and the availability of your AWS services and accounts. You can use AWS Health events to learn how service and resource changes might affect your applications running on AWS. AWS Health provides relevant and timely information to help you manage events in progress. AWS Health also helps you be aware of and to prepare for planned activities.
- AWS License Manager is a service that makes it easier for you to manage your software licenses from software vendors (for example, Microsoft, SAP, Oracle, and IBM) centrally across AWS and your on-premises environments. This provides control and visibility into the usage of your licenses, enabling you to limit licensing overages and reduce the risk of non-compliance and misreporting.
- AWS Step Functions provides useful guarantees around task assignments. It ensures that a task is never duplicated and is assigned only once.
- AppSync pipeline resolvers offer an elegant server-side solution to address the common challenge faced in web applications—aggregating data from multiple database tables. Instead of invoking multiple API calls across different data sources, which can degrade application performance and user experience, AppSync pipeline resolvers enable easy retrieval of data from multiple sources with just a single call. By leveraging Pipeline functions, these resolvers streamline the process of consolidating and presenting data to end-users.
- Though a private VIF is typically used to connect to a VPC, in the case of running an IPSec VPN over the top of a DX connection it is necessary to use a public VIF.
- You can use the managed prefix list for CloudFront as a part of your inbound rules in security groups that you attach to your origin resources, such as your EC2 instances or Application Load Balancers. The AWS-managed prefix lists are created and maintained by AWS and are available to use at no additional cost.
- A transit gateway is a network transit hub that you can use to interconnect your virtual private clouds (VPCs) and on-premises networks. You can attach the following to a transit gateway:
- One or more VPCs
- A Connect SD-WAN/third-party network appliance
- An AWS Direct Connect gateway
- A peering connection with another transit gateway
- A VPN connection to a transit gateway
- includes a VPN attachment with BGP for an AWS Transit Gateway. This allows BGP equal-cost multipathing (ECMP) to be used which can load balance traffic across multiple EC2 instances. This is the only solution that provides the ability to horizontally scale the outbound internet traffic across multiple appliances with HA across AZs.
- The DynamoDB global tables solution is the only database solution that will allow writes in both AWS Regions.
- NLBs do not have security groups configured and pass connections straight to EC2 instances with the source IP of the client preserved (when registered by instance-id).
- The other settings you can configure with the Block Public Access Feature are:
- BlockPublicAcls – PUT bucket ACL and PUT objects requests are blocked if granting public access.
- BlockPublicPolicy – Rejects requests to PUT a bucket policy if granting public access.
- RestrictPublicBuckets – Restricts access to principles in the bucket owners’ AWS account.
- In general, you can improve the transfer speed from your data source to the Snowball in the following ways, ordered from largest to smallest positive impact on performance:
- Use the latest Mac or Linux Snowball client
- Batch small files together
- Perform multiple copy operations at one time
- Copy from multiple workstations
- Transfer directories, not files
- it would be better to generate the CUR from the management account of the organization and then use QuickSight to visualize it. Permissions can be granted to the manager of the development OUs to view data relating to the individual accounts in each OU.
Serverless Services
- Lambda
- API Gateway
- S3
- DynamoDB
- SQS
- SNS
- SES
- EventBridge