Gateway is most likely going to be preferred all the time at the exam free for gateway, $ for interface endpoint.
- VPC
- e.g
192.168.1.0/242^(32-24)ip addresses - Network Address: 192.168.1.0
- Usable Host Range: 192.168.1.1 to 192.168.1.254
- Broadcast Address: 192.168.1.255
- e.g
- Subnet
- belongs to a VPC
- CIDR:
10.10.0.0/24-> 251 ip addresses - AWS reserved 5 IPs for specific usage (0-4, 255)
- Internet gateway & Route Table
- Internet gateway for components to connect to outside internet
- Bastion Hosts
- NAT
- Instances (outdated)
- Gateway
- NACL
- Network Access Control List (the top frontend)
- Stateless compared to SG (stateful)
- VPN
- Virtual Private Network
- Direct Connect
VPC
- virtual private cloud
- max 5 VPCs per region
- max 5 CIDR per VPC
- min size is 28 (16 IPs)
- max size is 16 (65536 IPs)
- private IPv4 ranges
10.0.0.0/8172.16.0.0/12192.168.0.0/16
- subnets
- CIDR block
10.0.0.0/24- .0 - network address
- .1 - VPC router
- .2 mapping to amazon provided DNS
- .3 - future usage
- .255 - network broadcast address (but not support in a VPC)
- CIDR block
- internet gateway
- allows resources in a VPC connect to the internet
- must be created separately from a VPC
- one VPC can only be attached to one IGW and vice versa
- IGW on their own do not allow internet access
- route table must be edited
- bastion hosts
- to SSH into private EC2
- NAT Instance
- NAT gateway
- AWS-managed NAT Gateway, higher bandwidth, high availability, no administration
- Pay per hour for usage and bandwidth
- NATGW is created in a specific Availability Zone, uses an Elastic IP
- Can’t be used by EC2 instance in the same subnet (only from other subnets)
- Requires an IGW (Private Subnet => NATGW => IGW)
- 5 Gbps of bandwidth with automatic scaling up to 100 Gbps
- No Security Groups to manage / required
- resilient within a single AZ
- must create multiple NATGW in multiple AZ for fault-tolerance
- NACL
- NACL are like a firewall which control traffic from and to subnets
- One NACL per subnet, new subnets are assigned the Default NACL
- You define NACL Rules:
- Rules have a number (1-32766), higher precedence with a lower number
- First rule match will drive the decision
- Example: if you define #100 ALLOW 10.0.0.10/32 and #200 DENY 10.0.0.10/32, the IP address will be allowed because 100 has a higher precedence over 200
- The last rule is an asterisk (*) and denies a request in case of no rule match
- AWS recommends adding rules by increment of 100
- Newly created NACLs will deny everything
- NACL are a great way of blocking a specific IP address at the subnet level
- VPC Peering
- Privately connect two VPCs using AWS’ network
- Make them behave as if they were in the same network
- Must not have overlapping CIDRs
- VPC Peering connection is NOT transitive (must be established for each VPC that need to communicate with one another)
- You must update route tables in each VPC’s subnets to ensure EC2 instances can communicate with each other
- can be created between VPCs in different AWS accounts/regions
- can reference a SG in a peered VPC
- VPC Endpoints (PrivateLink)
- Every AWS service is publicly exposed (public URL)
- VPC Endpoints (powered by AWS PrivateLink) allows you to connect to AWS services using a private network instead of using the public Internet
- They’re redundant and scale horizontally
- They remove the need of IGW, NATGW, … to access AWS Services
- types
- Interface Endpoints (PrivateLink)
- provisions an ENI as an entry point (must attach a SG)
- supports most AWS Services
- $ per hour + $ per GB processed
- gateway Endpoints
- provisions a gateway and must be used as a target in a route table
- supports both S3 and DynamoDB
- Free
- Interface Endpoints (PrivateLink)
- interface endpoint is preferred access is required from on-premises (S2S VPN or Direct Connect), a different VPC or a different Region
- VPC Flow Logs
- Capture information about IP traffic going into your interfaces
- VPC Flow Logs
- Subnet Flow Logs
- Elastic Network Interface (ENI) Flow Logs
- Helps to monitor & troubleshoot connectivity issues
- Flow logs data can go to S3, CloudWatch Logs, and Kinesis Data Firehose
- Captures network information from AWS managed interfaces too: ELB, RDS,
ElastiCache, Redshift, WorkSpaces, NATGW,Transit Gateway…
- Capture information about IP traffic going into your interfaces
- Site to Site VPN
- Virtual Private Gateway
- enable Route Propagation for VPG in the route table that is associated with your subnets
- Customer Gateway
- software application or physical device on customer side of the VPN connection
- Virtual Private Gateway
- VPN CloudHub
- provide secure communication between multiple sites
- low-cost hub-and-spoke model for primary or secondary network connectivity between different locations (VPN only)
- Direct Connect
- Provides a dedicated private connection from a remote network to your VPC
- Dedicated connection must be setup between your DC and AWS Direct Connect locations
- You need to setup aVirtual Private Gateway on your VPC
- Access public resources (S3) and private (EC2) on same connection
- Use Cases:
- Increase bandwidth throughput - working with large data sets – lower cost
- More consistent network experience - applications using real-time data feeds
- Hybrid Environments (on premise + cloud)
- Supports both IPv4 and IPv6
- If you want to setup a Direct Connect to one or more VPC in many different regions (same account), you must use a Direct Connect Gateway
- connection types
- dedicated connections - 1Gbps, 10Gbps, 100Gbps
- Hosted Connections - 50M, 500M, 10G
- Transit Gateway
- For having transitive peering between thousands of VPC and on-premises, hub-and-spoke (star) connection
- Regional resource, can work cross-region
- Share cross-account using Resource Access Manager (RAM)
- You can peer Transit Gateways across regions
- RouteTables: limit which VPC can talk with other VPC
- Works with Direct Connect Gateway,VPN connections
- Supports IP Multicast (not supported by any other AWS service)
- VPC Traffic Monitoring
- allows you to capture and inspect network traffic in your VPC
- route the traffic to security appliance that you manage
- capture the traffic
- capture all packets (or with filter)
- IPv6 in VPC
- IPv4 cannot be disabled for your VPC and subnets
- Egress-only Internet gateway
- used for IPv6 only
- must update route table
- AWS Network Firewall
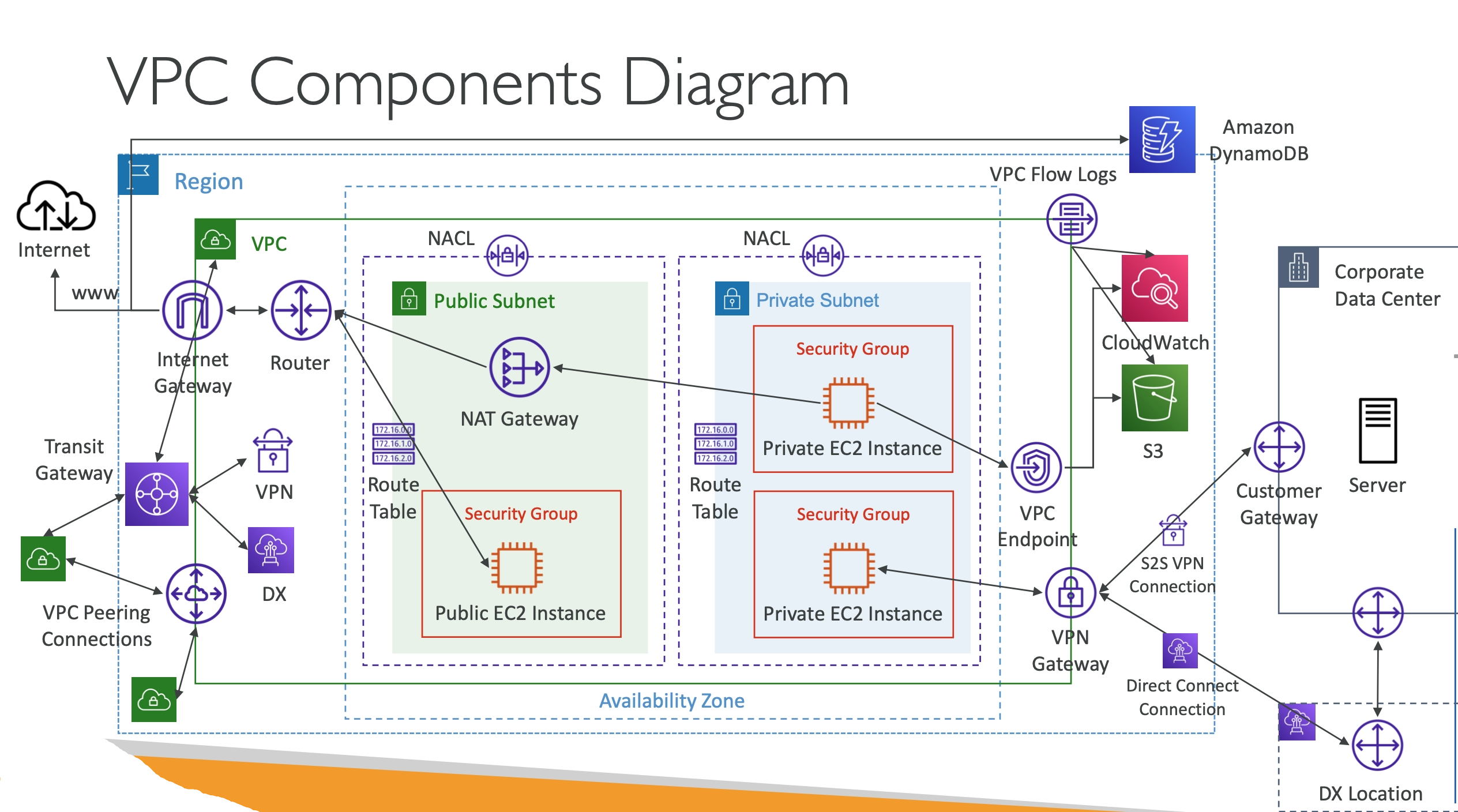
Summary
- CIDR – IP Range
- VPC – Virtual Private Cloud => we define a list of IPv4 & IPv6 CIDR
- Subnets – tied to an AZ, we define a CIDR
- Internet Gateway – at the VPC level, provide IPv4 & IPv6 Internet Access
- Route Tables – must be edited to add routes from subnets to the IGW,VPC Peering Connections,VPC Endpoints, …
- Bastion Host – public EC2 instance to SSH into, that has SSH connectivity to EC2 instances in private subnets
- NAT Instances – gives Internet access to EC2 instances in private subnets. Old, must be setup in a public subnet, disable Source / Destination check flag
- NAT Gateway – managed by AWS, provides scalable Internet access to private EC2 instances, when the target is an IPv4 address
- NACL – stateless, subnet rules for inbound and outbound, don’t forget Ephemeral Ports
- Security Groups – stateful, operate at the EC2 instance level
- VPC Peering – connect two VPCs with non overlapping CIDR, non-transitive
- VPC Endpoints – provide private access to AWS Services (S3, DynamoDB, CloudFormation, SSM) within a VPC
- VPC Flow Logs – can be setup at the VPC / Subnet / ENI Level, for ACCEPT and REJECT traffic, helps identifying attacks, analyze using Athena or CloudWatch Logs Insights
- Site-to-Site VPN – setup a Customer Gateway on DC, a Virtual Private Gateway on VPC, and site-to-site VPN over public Internet
- AWS VPN CloudHub – hub-and-spoke VPN model to connect your sites
- Direct Connect – setup a Virtual Private Gateway on VPC, and establish a direct private connection to an AWS Direct Connect Location
- Direct Connect Gateway – setup a Direct Connect to many VPCs in different AWS regions
- AWS PrivateLink / VPC Endpoint Services:
- Connect services privately from your service VPC to customers VPC
- Doesn’t need VPC Peering, public Internet, NAT Gateway, Route Tables
- Must be used with Network Load Balancer & ENI
- ClassicLink – connect EC2-Classic EC2 instances privately to your VPC
- Transit Gateway – transitive peering connections forVPC,VPN & DX
- Traffic Mirroring – copy network traffic from ENIs for further analysis
- Egress-only Internet Gateway – like a NAT Gateway, but for IPv6 targets
Quick Catchup
- AWS VPN CloudHub allows you to securely communicate with multiple sites using AWS VPN. It operates on a simple hub-and-spoke model that you can use with or without a VPC.