core concepts
- Identity and Access Management, Global Service
- Root account created by default, shouldn’t be used (to access service) or shared.
- Users are people within your organization, and can be grouped
- Groups only contain users
- Users don’t have to belong to a group, can belong to multiple groups
IAM Policies
Least Privilege Principle
- Sid: an identity for the statement
- Effect: Allow | Deny
- Principle: account/user/role to which this policy applies to
- Action: list of actions this policy allows or denies
- Condition: condition for when this policy is in effect
|
|
Condition Operators
- String - StringEquals, StringNotEquals, StringLike
- Numeric
- Date
- Boolean
- (Not)IpAddress
Condition: {"IpAddress": {"aws:SourceIp": "203.0.113.0/24"}}
- ArnEquals, ArnLike
- Null
IAM Policies Variables and Tags
- AWS Specific
- aws:CurrentTime, aws:TokenIssueTime, aws:principaltype, aws:SecureTransport
- Service Specific
- s3:prefix, s3:max-keys, s3:x-amz-acl, sns:Endpoint, sns:Protocol
- tag based
- iam:ResourceTag/key-name, aws:PrincipalTag/key-name
AWS IAM Boundaries
- IAM permission boundaries are supported for users and roles (not groups)
- advanced features to use a managed policy to set the maximum permissions an IAM entity can get
IAM Access Analyzer
- find out which resources are shared externally
- define zone of trust = AWS Account or AWS organization
- access outside zone of trusts => findings
- IAM Access Analyzer Policy Validation
- validates your policy against IAM policy grammar and best practices
- general warnings, security warnings, errors
- provides actionable recommendations
- IAM Access Analyzer Policy Generation
- generate IAM policy based on access activity
- CloudTrail logs is reviewed to generate the policy with the fine-grained permissions and the appropriate actions and services
- reviews CloudTrail logs for up to 90 days
Using STS to assume a Role
- define an IAM role within your account or cross-account
- define which principals can access this IAM role
- use AWS STS to retrieve credentials and impersonate the IAM role you have access to (AssumeRoleAPI)
- temporary credentials can be valid between 15 minutes to 12 hour
Session Tags in STS
- tags that you pass when you assume an IAM role or federate user in STS
aws:PrincipalTagStringEquals: "aws:PrincipalTag/Department": "HR"
MFA (Multi Factor Authentication)
MFA = password you know + security device you own
Access AWS
- AWS Management Console (pass + MFA)
- CLI (access keys)
- SDK (access keys)
select your user (don’t use the root), create access key & secret for awscli or SDK.
IAM Roles for Services
- Some [[AWS]] service will need to perform actions on your behalf
- To do so, we need assign permissions to [[AWS]] services with IAM Roles
- Common Roles
- EC2 Instance Roles
- Lambda Function Roles
- Roles for CloudFormation
IAM Security Tools
- IAM Credentials Report (account level)
- list all your account’s users and the status of their various credentials
- IAM Access Advisor (user level)
- show the service permissions granted to a user and when those services were last accessed
Organizations
- Global service
- Allows to manage multiple AWS accounts
- The main account is the management account
- Other accounts are member accounts
- Member accounts can only be part of one organization
- Consolidated Billing across all accounts - single payment method
- Pricing benefits from aggregated usage (volume discount for EC2, S3…)
- Shared reserved instances and Savings Plans discounts across accounts
- API is available to automate AWS account creation
- advantages
- multi-account vs one account Multi VPC
- use tagging standards for billing purposes
- enable cloud-trail on all accounts, send logs to central S3 account
- send cloud-watch logs to central logging account
- establish cross account roles for admin purposes
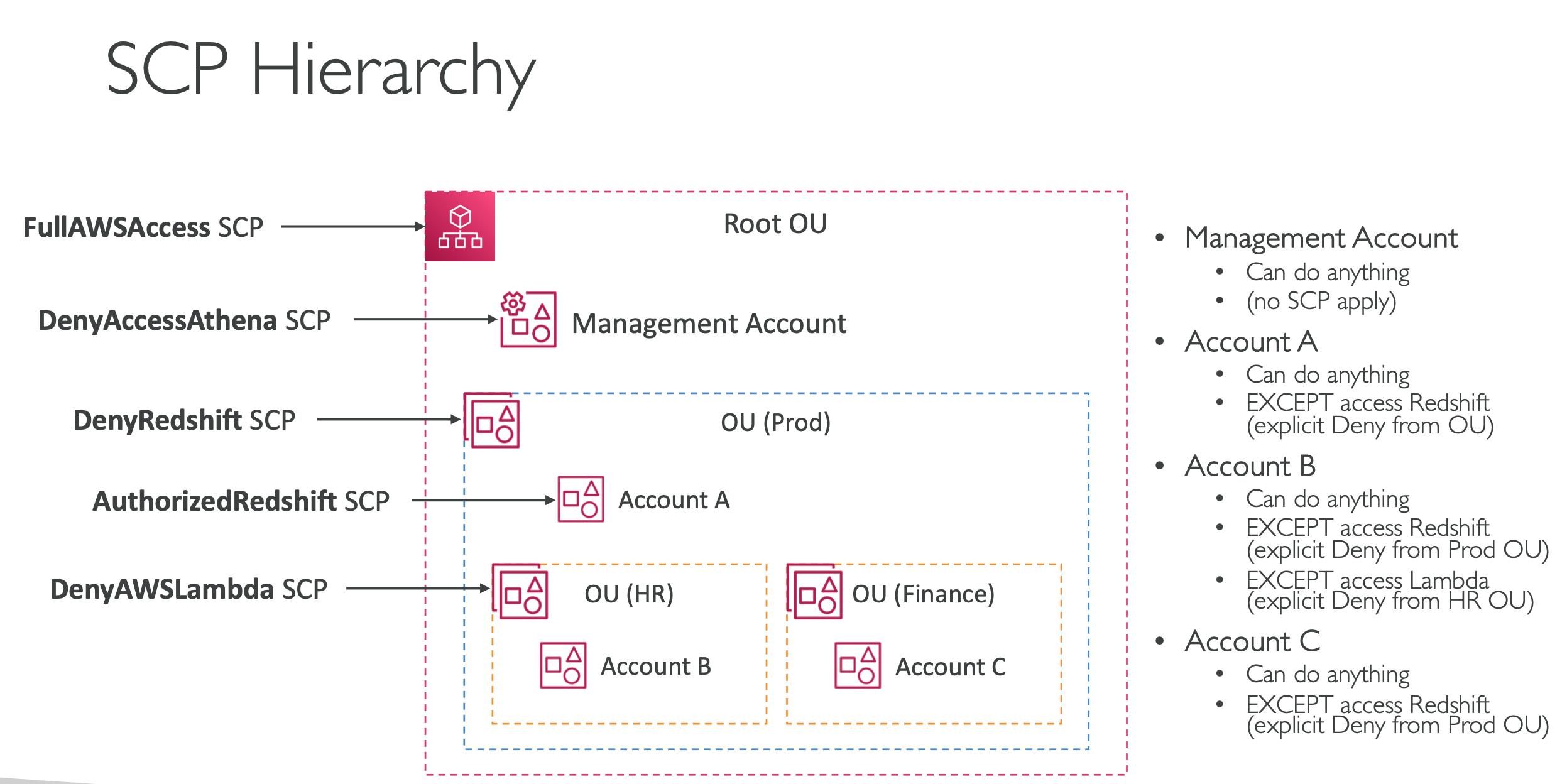
- security - service control policies
- IAM policies applied to OU1 or accounts to restrict users and roles
- don’t affect management account (full admin power)
- must have an explicit allow
aws:PrincipalOrgIdto be used in any resource policies
|
|
IAM Roles vs Resource Based Policies
- cross account
- attaching a resource-based policy to a resource - s3 bucket policy
- or using a role as a proxy
- when you assume a role, you give up your original permissions and take the permissions assigned to the role
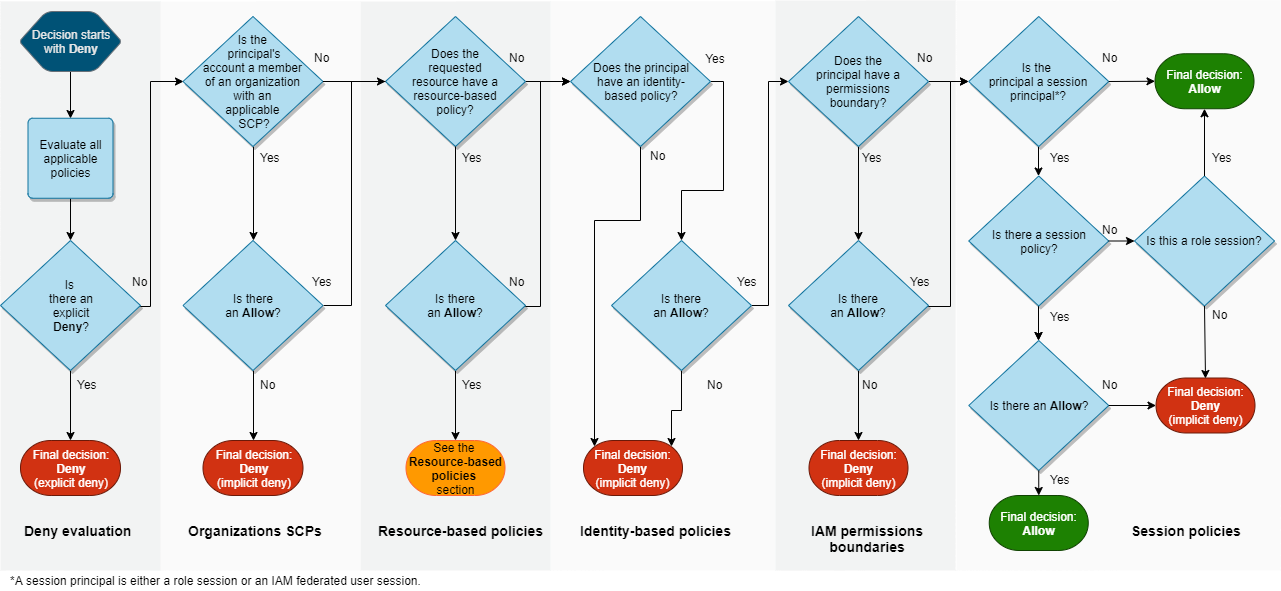
Request Authorization Flow Chart
restrict tags with IAM policies
- using
aws:TagKeysCondition key- validate the tag keys attached to a resource against the tag keys in the IAM policy
- use either
ForAllValuesorForAnyValue - use SCP to restrict creating resources without appropriate
Tags
|
|
AWS Organization Tag Policies
- helps you standardize tags across resources
- ensure consistent tags, audit tagged resources, maintain proper resources categorization
- helps with AWS Cost Allocation Tags and Attribute-based access control
- prevent any non-compliant tagging operations on specified services and resources
- generate a report that lists all tagged/non-compliant resources
- use amazon event-bridge to monitor non-compliant tags
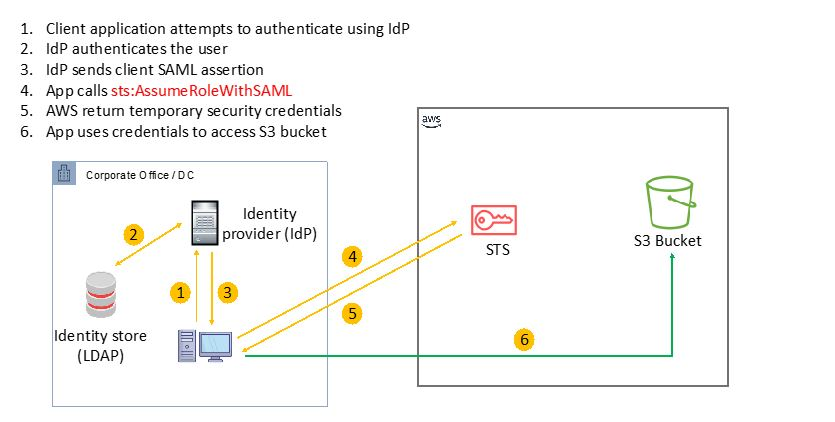
AWS IAM Identity Center
- one login (single sign-on) for all
- AWS accounts in AWS organizations
- business cloud applications
- SAML2.0-enabled applications
- EC2 windows instances
- identity providers
- IAM Identity Center
- 3rd party - active directory, OneLogin,
Okta
- permissions and assignments
- multi-account permissions
- application assignments
- attribute-based access control
Microsoft Active Directory
- Found on any Windows Server with AD Domain Services
- Database of objects: User Accounts, Computers, Printers, File Shares, Security Groups
- Centralized security management, create account, assign permissions
- Objects are organized in trees
- A group of trees is a forest
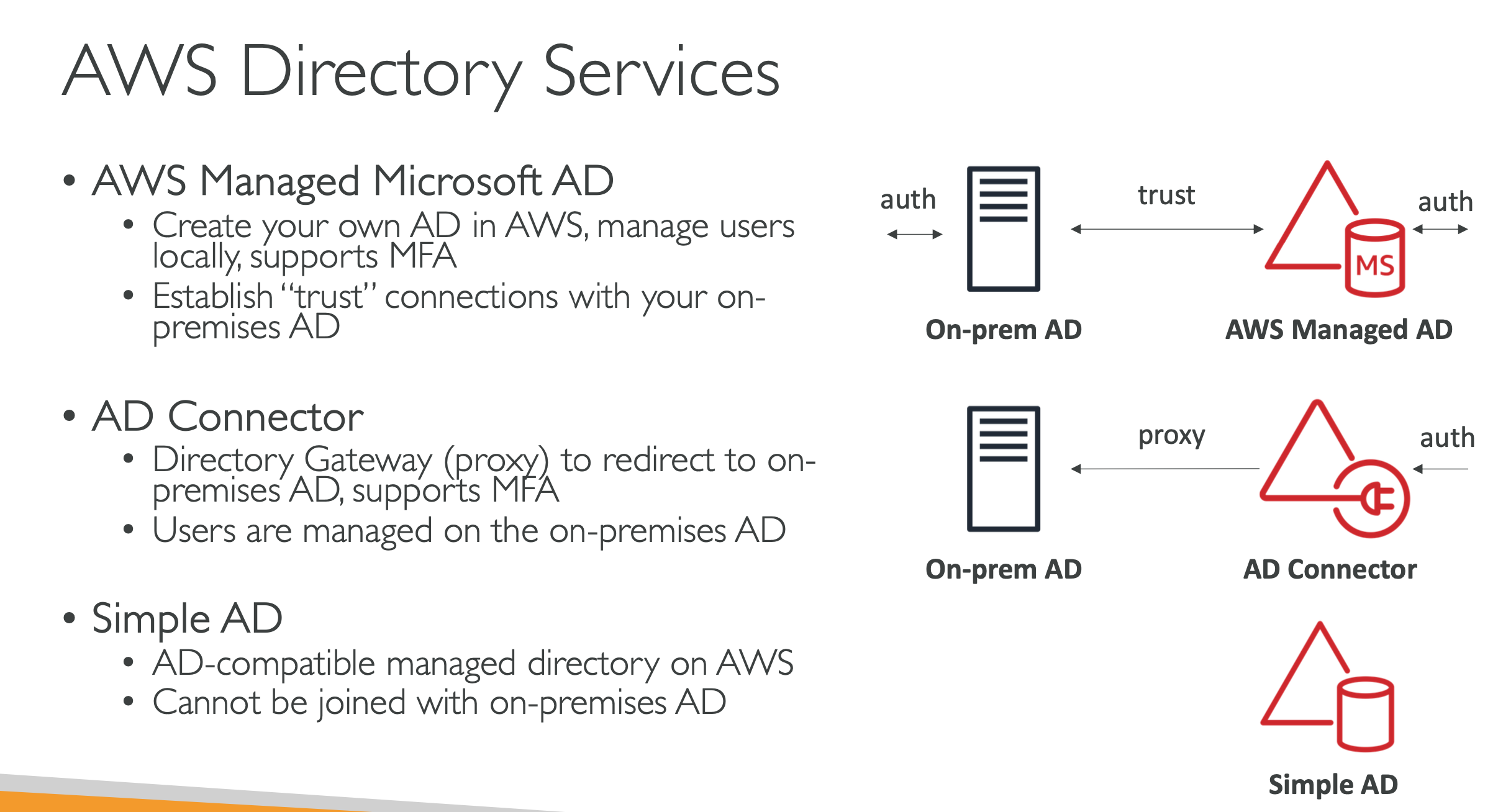
AWS Directory Services
- AWS Managed Microsoft AD
- AD connector
- Simple AD
AWS Control Tower - Guardrails
- Easy way to set up and govern a secure and compliant multi-account AWS environment based on best practices
- AWS Control Tower uses AWS Organizations to create accounts
- Benefits:
- Automate the set up of your environment in a few clicks
- Automate ongoing policy management using guardrails
- Detect policy violations and remediate them
- Monitor compliance through an interactive dashboard
- Provides ongoing governance for your Control Tower environment (AWS Accounts)
- Preventive Guardrail – using SCPs (e.g., Restrict Regions across all your accounts)
- Detective Guardrail – using AWS Config (e.g., identify untagged resources)
Best Practices
- Don’t use the root account except for AWS account setup
- One physical user = One AWS user
- Assign users to groups and assign permissions to groups
- Create a strong password policy
- Use and enforce the use of MFA
- Create and use Roles for giving permissions to AWS services
- Use Access Keys for CLI/SDK
- Audit permissions of your account using IAM Credentials Report & IAM Access Advisor
- Never share IAM users & Access Keys
-
Organization Unit ↩︎